Back to blogs
Aniruddh Balasubramaniam
Jun 16, 2025
In today's hyperconnected world, forming new connections is effortless. But with ease comes risk: unwanted messages, relentless spam, and invasive privacy breaches. Traditional contact methods—phone numbers and email addresses—are permanent, easily shared without consent, and shockingly vulnerable to misuse.
Enter Port: The revolutionary solution that replaces static contact information with dynamic, permission-based "Ports." Whether you're meeting someone face-to-face, forging online friendships, accepting introductions, or publishing your contact details publicly, Port ensures every interaction remains private, reversible, and always under your control.
1. Meeting in Person: Show a Port QR Code, Not Exchange Numbers
The Old Way: When two people strike up a conversation at a café, conference, or networking event, the instinctive way to stay connected is by swapping phone numbers. Once exchanged, there’s no turning back: unsolicited calls and messages can start arriving at any moment.
With Port: Simply generate a one-time Port QR code on your device. The other person scans it, and boom – you're connected.
Why It’s Better:
· Instant & Paperless: No more fumbling for cards or risking miswritten digits.
· One-Time Use: Each Port QR is designed for a single scan, providing total peace of mind.
· Fully Reversible: Unlike phone numbers, Ports leave no lasting identifier. You can disconnect at any time—no strings attached.
2. Meeting Online: Share a Safe Link Instead of a Number
The Old Way: Moving a conversation from a dating app or professional forum to a "more reliable" channel often means exchanging private phone numbers or personal email addresses. Handing over your number to someone you barely know can lead to awkward follow-ups or messages you'd rather not receive.
With Port: You generate a one-time Port link instead. They click, connect, and their access is automatically governed by your Port’s settings.
Why It’s Better:
· One-Time Use: Once clicked, the Port is invalidated—total peace of mind.
· Fully Reversible: Maintain complete control. Disconnect at any time, leaving no permanent identifier.
· Permissioned Access: Define exactly how new connections can interact with you, from the start.
3. Friend Introductions: Only Let Trusted Contacts vouch for You
The Old Way: Our social and professional circles often expand through mutual acquaintances. A friend introduces you to someone new, assuming their trust in you extends to the newcomer. But the moment your contact info is shared, it can be forwarded indiscriminately, often reaching people you'd rather not connect with.
With Port: Your friend generates a Port on your behalf—only that Port can be used to connect you with their contact.” Only your trusted friends can generate Ports that connect to you.
Why It’s Better:
· Controlled Referrals: Only approved friends can share your Port.
· Awareness: You know how a new connection came to be. You know who shared your contact with whom.
· One-Time Use: Your friends can only create one-time use Ports that connect to you. This way, a bad friend can’t misuse this permission.
4.Publishing Contact Details: Swap Static Info for Re-usable Ports
The Old Way: Whether it’s a “Contact Us” section on your website or a physical poster at a community event, publishing an email or phone number invites everyone—and anyone—to reach out. Marketing inquiries, spam bots, telemarketers, and even malicious actors can flood your inbox.
With Port: Create a "Re-usable Port" specifically designed for public display. Set limits on how many people can connect, and define what kind of messages they can send (e.g., text only, no calls). All new conversations are neatly organized within Port, separate from your personal inbox. Once your desired number of connections is reached, the Port automatically expires, stopping unsolicited outreach.
Why It’s Better:
· Organized Connections: Each incoming conversation is compartmentalized—no more hunting through junk to find real connections.
· Gated Access & Spam Prevention: Control the flow of inquiries. Once your campaign goal is met, the Port closes itself, cutting off spam at the source. You also retain the power to delete the Port instantly, anytime.
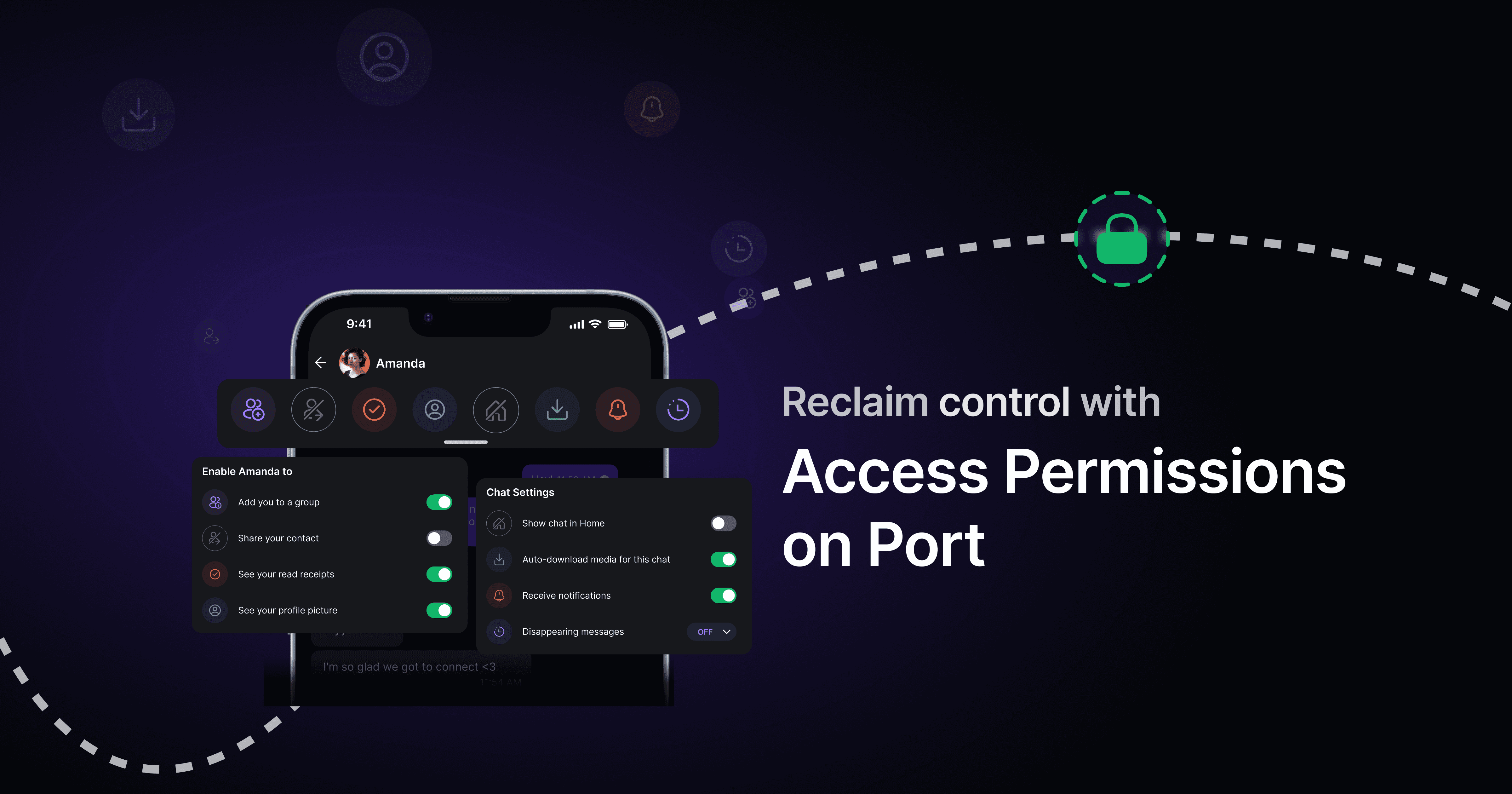
Port: Putting YOU Back in Control.
Port is a complete rethink of how we connect. Here’s how it keeps you in the driver’s seat:
· No contact info used (or any static identifiers): No more phone numbers, email addresses, or social handles floating around in the wild.
· Granular Permissions: Define who can connect, when, and for how long.
· Reversible: If a contact is misusing the access you’ve given them, you can revoke access instantly.
· Seamless Integration: Whether you’re networking at an event, chatting on an app, relying on friends’ referrals, or listing your details publicly, Port fits naturally into each scenario.
By replacing static identifiers with dynamic, cryptographically secure Ports, you eliminate the risk of unwanted outreach, spam, and privacy leaks—while still making genuine connections effortlessly easy.
Ready to experience better, safer connections? Visit portmessenger.com to learn more..
Other articles:
Jun 8, 2024
Going Numberless
Aniruddh Balasubramaniam
Read more
Jun 10, 2024
Connect on your terms … starting now
Janice Coutinho
Read more
Jun 12, 2024
How "Ports" work (vs phone numbers)
Aniruddh Balasubramaniam
Read more
Jun 14, 2024
Resuable Ports - the smart way to network
Aniruddh Balasubramaniam
Read more
Jun 16, 2024
Why is Port a better way to connect?
Janice Coutinho
Read more
Jun 20, 2024
What is a Port?
Abhinav
Read more
Jun 29, 2024
Blocking a user without public identifiers
Abhinav
Read more
Aug 2, 2024
How Port puts you in control
Janice Coutinho
Read more
Aug 7, 2024
How does Port make secure, identifier-less, end-to-end encrypted chats?
Shantanav Saurav
Read more
Aug 29, 2024
Sharing A Contact: The Numberless Way
Shantanav Saurav
Read more
Sep 9, 2024
Building a new avatar set for Port
Amudhasurabhi Aravindan
Read more
Oct 8, 2024
How Port is using design thinking to address diverse user needs
Ruthvik V
Read more
Jan 23, 2025
Redefining Privacy with Port's Access Controls within 24 hours
Sagarika SV
Read more
Apr 14, 2025
Designing Port’s new Masterflow: A control unit for clarity
Sagarika SV
Read more
Jul 21, 2025
We’re making Port open-source
Aniruddh
Read more